[HackTheBox] Devel
This is also a really simple box. Intuitive as well. I can say I was able to solve this box within 15 minutes due to past experience and availability of exhaustive notes.
Reconnaissance:


So I tried putting a text file and well, it worked.
Foothold:

This hi.txt was reflecting on the website. so we can put a .aspx revshell

This gave me temporary euphoria when I saw system32, put well…. I wasn’t root.
Privilege Escalation:

So, PrintSpoofer should work here. Spoiler Alert: It doesn’t. :(

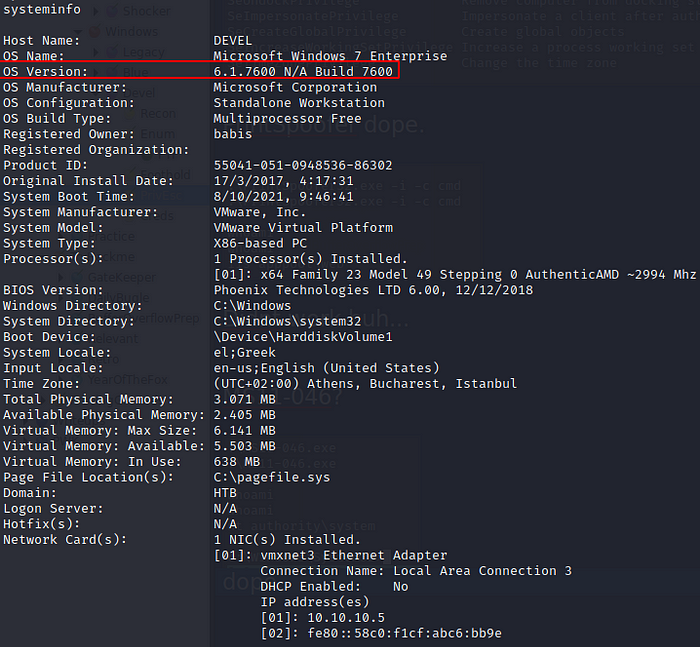
System Info Reveals the OS Version. A quick google gives an open privilege escalation exploit.

PWNED!!!
After Thought:
Now this box could have made me bang my head over the fact that the initial attempt at a php webshell didn’t work and PrintSpoofer32.exe didn’t work either, but I had a lot of notes for the many machines I have completed with me. So I basically looked up the different Windows machines and thought of the system exploit first because they are the easiest to rule out in windows. This time I got Lucky with the first open system exploit I looked at. If I did not find that, I would have scrounged the download and document files for some user downloaded programs followed by registry keys permissions.
