[HackTheBox] Brainfuck
This Box is really twisted but very interesting.
Reconnaissance:
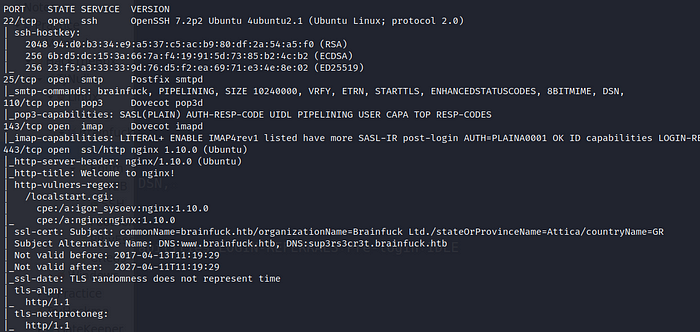
Enumeration:
WEB → https://brainfuck.htb


Lets run a quick wpscan.

We found “admin” and “administrator” users but their brute force led to nowhere.
This gets us into the admin dashboard and we can look at mail password of orestis.

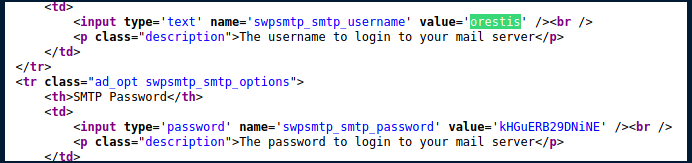
pop3 → Has 2 mails for orestis one of which gives some hint

Now we move to sup3rs3cr3t.brainfuck.htb and login


Since we can see that orestis has a signature i.e. “ Orestis: Hacking for fun and profit” we can try manipulating the words to get a clear cipher.
Many rounds of custom Caesar cipher didn’t give anything, then a hint from a HTB hacker led me to vignerre cipher.

Foothold:
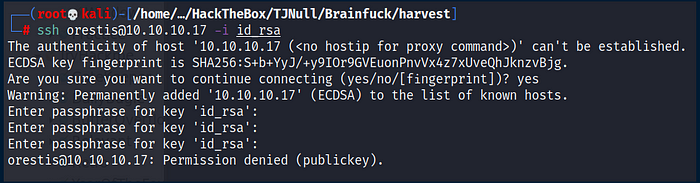
Irritating af…
ssh2john.py id_rsa > hash ; john hash — wordlist=/usr/share/wordlists/rockyou.txt
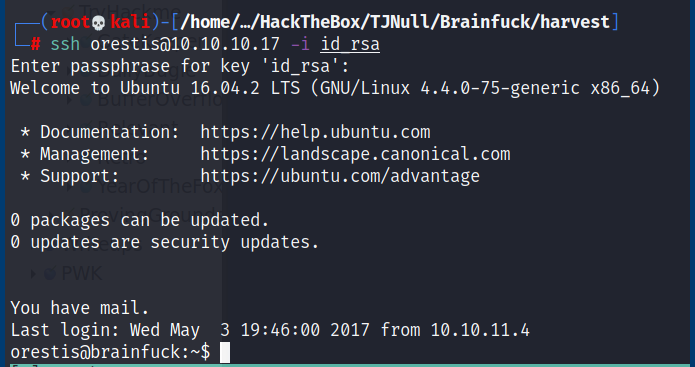
Privilege Escalation:

OOOOOO. lxd vulnerable. PWNED.
All in all this box has a lot of stuff that's not the optimum when it comes to preparing for OSCP but It has intuitive stuff there.
